In this tutorial I am going to show you how to set up and deploy an Always-On P2S (Point-to-site) VPN to Azure, allowing you to access your Azure resources remotely. I am going to walk you through how to create a Virtual Network Gateway through the Azure Management Portal, configure the point-to-site connection, create a VPN profile and deploy that to your end users using Microsoft Intune.
The goal with our scenario is to expand on our current Azure environment by implementing a Point 2 Site VPN that is ‘Always On’. Users will authenticate to the VPN using their Azure Active Directory credentials.
Page Contents
- Current environment
- Create and configure a Virtual Network Gateway
- Authorise the Azure VPN Client
- Configure the P2S VPN settings
- Manually test the Azure VPN Client
- Deploy the Azure VPN Client using Microsoft Intune
- Configure your VPN profile
- Deploy your VPN profile using Microsoft Intune
- End user experience
Current environment
Let’s take a look at our current environment. For the purpose of this tutorial, our environment is very simple. We have a single VNET, that contains a single Subnet and connected to that subnet is a virtual machine running Windows Server 2022.
Below is our IP addressing schema. If you are familiar with Azure, you may notice that these are the default settings when you build a VNET, Subnet and Virtual Machine.
- VNET Address space: 10.0.0.0/16
- Subnet: 10.0.0.0/24
- Virtual Machine: 10.0.0.4

Once we have built our Always-On Azure VPN deployment, I will share the updated diagram image below.
Create and configure a Virtual Network Gateway
The first thing we need to implement into our environment is a Virtual Network Gateway. Behind the scenes, a Virtual Network Gateway is 2 virtual machines which run gateway services and contain specific routing information. When we set up our Virtual Network Gateway, we just see a settings blade in the Azure Portal which we can configure to achieve our desired results.

3. Search for Virtual Network Gateway in the Marketplace and select it from the list. The Virtual Network Gateway page will appear, then click Create.

4. You will now be at the gateway configuration wizard. In the below screenshot, I have highlighted some important settings:
- Region: Ensure you choose the same region your VNET is deployed in.
- Gateway type: This must be set to VPN as that is what we want to deploy.
- VPN Type: Chose Route-based, as this supports VPN types including P2S, S2S and Inter-virtual network connections.
- SKU: I have selected the minimum supported SKU for my minimal setup. You should know that the Basic SKU does not support the type of P2S VPN we are going to deploy. You can use this reference as a sizing guide.
- Virtual network: Select your existing virtual network.

5. Scrolling down on the same page, we need to configure the network settings. I have left the suggested Gateway subnet address range as the default, but you can adjust it as required. For the remaining settings I have highlighted:
- Public IP Address: Type: Select Standard
- Public IP address: Select create new.
- Public IP address name: Enter a meaningful name for the public IP.

6. When you are ready, click Review + Create, then click Create. You will be presented with the deployment status page, this took around 27 minutes to complete, so allow it some time.

Authorise the Azure VPN Client
To use the Azure VPN Client on our end users’ machines we must first integrate it into our solution by authorising the app to sign in and read basic profile information.
Authorise the application with the following link:
You will be presented with the following page:

Click Accept and you are done with this step.
Configure the P2S VPN settings
We must now complete the Point-to-site configuration on our Virtual Network gateway.
1. Start by opening the Virtual Network Gateway in Azure and selecting Point-to-site configuration.

2. Click Configure now.

3. You need to fill out all of the options on the screen, here is some guidance on completing each option:
- Address pool: This is the subnet in which VPN client users will receive an IP when they connect to the VPN. This should be a subnet that is not being used in Azure, outside of the available Azure VNET address space to avoid conflicts.
- Tunnel type: This should be set to OpenVPN (SSL).
- Authentication type: Azure Active Directory will allow our directory users to authenticate to the VPN with their work email and password.
- Tenant: https://login.microsoftonline.com/YOUR AZURE AD TENANT ID/
- Audience: YOUR AZURE VPN CLIENT APPLICATION ID
- Issuer: https://sts.windows.net/YOUR AZURE AD TENANT ID/
To find your Tenant ID: Azure Active Directory > Overview > Tenant ID
To find the Azure VPN client application ID: Azure Active Directory > Enterprise Applications > Azure VPN > Application ID

If there are any issues with the address pool configuration, you will likely see an error like:
Error: The virtual network gateway’s VPN client address pool overlaps with the virtual network’s address space.
It will also detail the overlapping address spaces to help you resolve and progress with the setup.
4. Once all the details have been entered, click Save at the top of the page.
Manually test the Azure VPN Client
Now we have configured our P2S VPN, we should test the connection works as expected before we pilot the deployment with Intune.

2. Now you need to download/install the Azure VPN client manually (just for testing). You can download the offline installer here. Or install it through the Microsoft Store.
If you download the offline installer, make sure you turn on Developer mode first (Settings > Privacy & security > For developers).

Then run the install script: (you have have to accept the security warning a few times)

3. Now the client is installed, open it from the Windows start menu, click the + symbol and click Import.

4. In the file explorer window, browse to the zip folder you downloaded and select the azurevpnconfig.xml file from within the AzureVPN folder and click Open.

5. Leave all the options on the screen as default and click Save. Click Connect and log in with your work account, the VPN should successfully connect. Take a moment to look at the connection properties and ensure the VPN routes look correct.

6. By default the Network Security Groups configured in Azure for your virtual machines will allow all traffic from your virtual network, however the local firewall on your virtual servers will not. Assuming you are running Windows, you will need to create a local firewall rule to allow the necessary range to access your server.

7. The final result should be that you can communicate with your Azure resources over the VPN.

Deploy the Azure VPN Client using Microsoft Intune
Now we have everything configured and tested, we can deploy the Azure VPN client to end user devices using Intune.
2. From the left-hand menu, select Apps > All Apps > Add.

3. From the App type drop down list, select Microsoft Store app (new) and click Select at the bottom.

4. Click Search the Microsoft Store app (new).

5. Search for the Azure VPN Client, click it once then click Select at the bottom of the page.

6. On the app information page there are various settings you can change. Most options can be left as default, however I have highlighted some you may want to change.

Regarding the image file, I retrieved this by navigating to https://apps.microsoft.com/ and searching for the Azure VPN Client, then right-clicking on the app image and saving the file. The file extension then needs to be changed to .png and it can be uploaded on the app information page above.
7. When ready, click Next, then Review + create.
8. Once the app is created, on the properties page, click Edit next to Assignments.

9. Under the Required heading, click Add group and select a group containing your pilot users (you should test with some volunteer users before deploying to all). In my case, I have selected All users. Then click Review + save.

Configure your VPN profile
We now need to configure our VPN profile and deploy it to our endpoints. Once the profile is installed on the device, the user will be prompted to log in to the VPN client and it will become active.
The profile will be in XML format and will be a combination of a template file I will provide below and the azurevpnconfig.xml you downloaded earlier in the .zip file.
1. Start by copy and pasting the below into a text editor: (I am using notepad ++)
<VPNProfile>
<!--<EdpModeId>corp.contoso.com</EdpModeId>-->
<RememberCredentials>true</RememberCredentials>
<AlwaysOn>true</AlwaysOn>
<TrustedNetworkDetection>contoso.com,test.corp.contoso.com</TrustedNetworkDetection>
<DeviceTunnel>false</DeviceTunnel>
<RegisterDNS>false</RegisterDNS>
<PluginProfile>
<ServerUrlList>azuregateway-7cee0077-d553-4323-87df-069c331f58cb-053dd0f6af02.vpn.azure.com</ServerUrlList>
<CustomConfiguration>
</CustomConfiguration>
<PluginPackageFamilyName>Microsoft.AzureVpn_8wekyb3d8bbwe</PluginPackageFamilyName>
</PluginProfile>
</VPNProfile>2. Now open your azurevpnconfig.xml file side by side with the code above.
3. Within the opened XML file copy, the fqdn ending in ‘.vpn.azure.com’ and place it between <ServerUrlList> </ServerUrlList> in the code above. Also, change the value between <TrustedNetworkDetection> </TrustedNetworkDetection> to your internal domain if required.
4. Now copy and paste the entire contents of the azurevpnconfig.xml file and paste it between <CustomConfiguration> </CustomConfiguration>.
5. Lastly, there will be a ‘name’ tag in your code, this is what mine looks like before changing it:
<name>rg-vm-fileserver1-vnet</name>
This is what will appear as the name of your VPN connection for your end users. By default it will be the name of the associated virtual network in Azure, so change this to something meaningful. For example I have set mine to
<name>OCN VPN</name>.
6. Save the file you have created so it is not lost.
Deploy your VPN profile using Microsoft Intune
To deploy our VPN profile we are going to use a custom configuration profile in Intune.
2. From the left-hand menu, select Devices.

3. Then select Configuration profiles.

4. Select Create profile.

5. On the Create a profile pop-out window, choose Windows 10, Templates, select custom from the template list and click Create.

5. Enter a name and description for your profile and click Next.

6. On the Configuration settings page click Add.

7. On the Add Row pop-out windows, complete the information:
- Name: choose a name for your config (this does not affect the deployment)
- OMA-URI: ./User/Vendor/MSFT/VPNv2/<name of your connection>/ProfileXML – Modify the text in bold to the name of your VPN profile, this should be the same as what you set between <name> </name> in your XML file. In my case, this is what I have used: “./User/Vendor/MSFT/VPNv2/OCN VPN/ProfileXML”
- Custom XML: Select the folder icon and upload the XML file you created ealier.

8. Once ready, click Save then Next.
9. On the assignments tab, include all the groups of users or devices you want to profile to apply to and click Next.
10. Click Next through the remaining settings and then click Review + save.
End user experience
For the end user, to begin with, once the Azure VPN Client is installed they will see the client appear in their Windows start menu:

Before the profile is deployed, there will be no further notification to the end users.
Once the VPN profile is deployed, which happens as soon as the device is synced with Intune, they will receive a pop-up notification and also a notification save in their notification area.
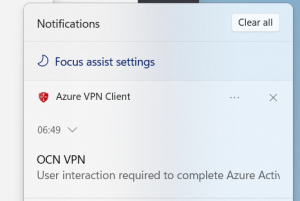
The user should click on the notification, then the Azure VPN Client will open.

All they will need to do is click Connect and login to the interactive login prompt with their work email and the VPN will connect successfully. You will notice that if they click Disconnect the VPN will automatically reconnect a second or two later.

Daniel, Thanks for your excellent explanation. One question – I’ve already manually deployed the VPN profile to users. If I want to now automatically deploy the same profile, what will happen to users who already have the profile deployed? I would like to assign the deployment to all users, without having to figure out which ones already have it deployed.
Regards,
GIl
Hi Gil!
In my experience, if you have manually created a profile already, deploying a profile with the same name for them users will cause a duplicate to appear.
Nothing that can’t be solved with some communication and a few screenshots! 🙂
Cheers
Dan
How did you manually deploy it to multiple end users I am looking for a way to do that please